The Future of Secure Access: Citrix ZTNA Unleashed
The rise of remote work, cloud adoption, and increasing cyber threats has forced companies to rethink their security approach. For IT departments, an IT security model with the philosophy of “Never Trust, Always Verify” takes centre stage – This is where Zero Trust Network Access (ZTNA) comes in.
In 2021, Citrix, a leader in secure digital workspaces, launched Secure Private Access as a modern alternative to VPNs and legacy security architectures. This service is a cloud delivered Zero Trust Network Access (ZTNA) solution. In this blog, we’ll explore why ZTNA is essential, how Citrix Secure Private Access enhances security, and how organizations can benefit from a Zero Trust approach.
What is Zero Trust Network Access (ZTNA)?
ZTNA is a security framework that ensures strict identity verification and least privilege access before allowing users and devices to connect to applications and data. Unlike traditional security models that trust users inside the corporate network, ZTNA:
- Authenticates continuously based on identity, device posture, and risk level.
- Limits access to only what is needed (least privilege access).
- Reduces the attack surface by segmenting applications and users.
- Supports remote work and hybrid environments securely.
ZTNA is particularly relevant as cyber threats evolve, and organizations move toward cloud-first strategies.
Why Traditional Security Models Are Failing
- VPNs are no longer enough – Traditional VPNs provide full network access, increasing security risks in a remote work environment.
- Lateral movement threats – Once an attacker breaches the network, they can move freely within the corporate environment.
- Complexity and poor user experience – Legacy security models introduce performance bottlenecks and impact productivity.
Organizations need a modern security solution that addresses these challenges without compromising performance.
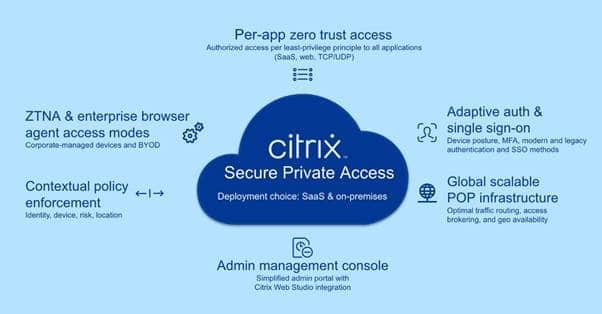
Citrix Secure Private Access: A ZTNA Solution
Citrix Secure Private Access is a comprehensive Zero Trust security solution that ensures secure access to all applications, whether they are hosted on-premises, in the cloud, or SaaS-based.
Key Features & Benefits
Zero Trust Per-App Access – Users get access only to the apps they need, reducing security risks. If an employee works remotely from an untrusted location, access policies dynamically adjust to restrict access to only essential applications. This prevents lateral movement and ensures sensitive data remains protected.
Context-Aware Policies – Access is granted based on device security posture, identity, and network conditions. If a user is logging in from a vulnerable public Wi-Fi network, Citrix Secure Private Access can enforce additional authentication factors or block access to high-risk applications. This approach ensures a tailored security response based on real-time conditions.
Agent & Agentless Access Modes – Supports both corporate-managed devices and BYOD (unmanaged devices). Employees using personal laptops or mobile devices can securely access corporate applications without requiring a full VPN connection. The system enforces security controls without interfering with personal device data, ensuring privacy and security coexist.
Secure SaaS & Web Access – Protects SaaS, web, and TCP/UDP apps without requiring VPNs. For example, remote contractors needing access to cloud-based CRM tools can securely connect without exposing the entire corporate network. The solution ensures secure connectivity while minimizing the risk of data leakage.
Integrated Single Sign-On (SSO) & MFA – Enhances security while improving user experience. Users authenticate once and gain seamless access to multiple applications, eliminating the need to remember multiple passwords. Multi-factor authentication (MFA) ensures only verified users can access critical business systems, reducing the risk of credential-based attacks.
End-to-End Observability – IT teams gain visibility into user access and application performance. Security teams can monitor access attempts in real time, detect anomalies, and take proactive measures against potential threats. Detailed logging and analytics provide insight into failed login attempts, unusual access patterns, and compliance violations.
ZTNA vs. VPN vs. Traditional VDI: What’s the Difference?
| Features | ZTNA (Citrix Secure Private Access) | VPN | Citrix traditional VDI (Virtual Desktop Infrastructure) / Any other VDI solution |
| Security Model | Zero Trust, least privilege access | Full network access | Fully virtualized desktop environment |
| User Experience | Seamless, per-app access | Latency issues, entire network access | Full desktop with managed apps and security policies |
| Access Control | Granular, policy-based | Broad access to corporate network | Centralized IT control over the desktop environment |
| Ideal Use Case | Secure cloud and SaaS access | Legacy remote work setups | Centralized desktop management for high-security environments |
Organizations that prioritize security, flexibility, and performance find that ZTNA is the ideal choice over traditional VPNs and Citrix Virtual Desktops for secure application access.
Use Cases & Industry Adoption
- Remote Work Security – Employees securely access apps from anywhere without VPN overhead.
- Contractor & Third-Party Access – Grant temporary, least-privilege access without exposing the entire network.
- BYOD & Unmanaged Devices – Provide secure access without forcing device enrolment. Organizations across industries are rapidly adopting Citrix Secure Private Access to modernize their security and improve workforce flexibility.
- Healthcare & Finance Compliance – Meet regulatory requirements (HIPAA, GDPR) with strong authentication controls.
- Government & Public Sector – Securely enable access for agencies handling classified and sensitive data while enforcing strict security protocols.
- Construction & Field Operations – Allow project teams and contractors to securely access applications and data from remote locations without requiring corporate devices.
Future Trends in Zero Trust Security
- AI & Machine Learning Integration – Automated threat detection and adaptive security controls.
- Cloud-Native Security Solutions – Secure multi-cloud & hybrid environments seamlessly.
- Policy Automation & Orchestration – Reduce admin overhead with intelligent policy enforcement.
- Advanced Threat Analytics – Real-time monitoring of user behaviour to detect anomalies.
Citrix is a strong choice for implementing ZTNA, especially with its strategic acquisition of Device Trust. This integration ensures that only authenticated and authorized devices can access your network, adding an extra layer of security to your zero-trust strategy. With enhanced device validation, Citrix not only verifies user credentials but also confirms the integrity and trustworthiness of the device accessing your resources. For more in-depth insights on how Citrix is advancing its Zero Trust approach, please refer to our detailed blog: Device Trust – Taking Your Zero Trust Strategy to the Next Level.
Why Citrix ZTNA is the Right Choice
Zero Trust is no longer an option—it’s a necessity for organizations looking to reduce risk, enable remote work, and secure their digital assets. Citrix Secure Private Access provides a seamless, scalable, and future-proof approach to implementing Zero Trust security.
- Enhance Security – Prevent unauthorized access with Zero Trust policies.
- Improve User Experience – No need for traditional VPNs, ensuring fast and secure access.
- Simplify IT Management – Centralized security controls and automated policy enforcement.
As businesses evolve, ZTNA is the way forward, and Citrix Secure Private Access is leading the way. Are you ready to secure your enterprise? Do consult ES Team for more information.
As Platinum Partner, Enterprise Solutions have the expertise to work with Citrix, their products and you to deliver your organisation a hybrid work model with the world’s leading Zero Trust vendor. If you have questions or insights to share? Email us at asktheexpert@enterprise-solutions.ie.

Narendra is a seasoned expert with over 18 years of experience in Mobility, Network Security, and Cloud. He has successfully designed and integrated End-User Computing (EUC) solutions across industries such as FSI, Banking, Manufacturing, Shipping, and Consulting. With a strong customer-first approach, he ensures seamless implementation, driving customer success and delivering tangible business value.




