Modern Cyber Threats to Your Staff: A Daily Reality for All Businesses
As digital transformations accelerate, the risk of cyber threats to identity has grown significantly, posing a substantial challenge for IT administrators and operations managers. In recent years, it has been reported that around 40% of companies worldwide experience some form of cyber breach annually. Understanding the types of cyber threats and leveraging tools like Microsoft Secure Score and programs like MicroWarehouse’s Mission 65 can bolster security measures and protect organisational integrity.
Common Cyber Threats to Identity
Cyber threats to identity can take numerous forms, each with its own set of challenges. These threats happen daily, regardless of the size of the company. Smaller companies are often targeted more frequently due to the higher security measures implemented by larger companies.
Phishing Attacks
Phishing is a widespread method where attackers deceive individuals into divulging sensitive information, such as login credentials. If an account is compromised, emails are often sent from that account to all its contacts. Consequently, you might receive an email from a familiar or trusted individual containing a Phishing link.
Credential Stuffing
This technique involves the use of automated tools to attempt large numbers of username and password combinations. Credential stuffing is highly effective when users reuse passwords across various platforms, thereby facilitating attackers in compromising multiple accounts.
Social Engineering
Social engineering exploits human psychology to manipulate individuals into breaking normal security procedures. Users can be manipulated to click on phishing links, respond to fake multi-factor authentication (MFA) prompts, or grant access to individuals who should not have it.
Malware and Ransomware
Malware, including ransomware, is malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. Ransomware encrypts victims’ data, only releasing it upon payment of a ransom, putting identities and sensitive information at risk.
Microsoft Secure Score: Enhancing Security Posture
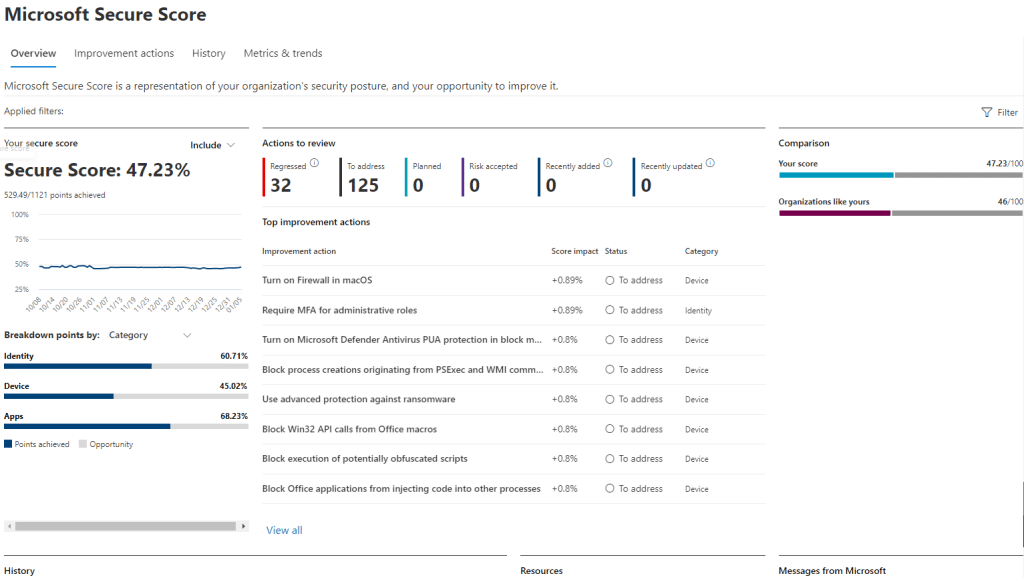
Microsoft Secure Score is a vital tool for IT admins and operations managers who are aiming to enhance their security measures. This feature is integrated into Microsoft 365, it provides a comprehensive measurement of an organisation’s security posture, offering actionable insights and recommendations to mitigate risks.
Key Features of Microsoft Secure Score
- Real-Time Visibility: Secure Score provides a dynamic overview of your current security posture, highlighting areas that need immediate attention.
- Actionable Recommendations: It offers specific, prioritized recommendations to improve security, tailored to your organisation’s unique environment.
- Measurable Impact: Each action item is assigned a score, allowing you to quantify the impact of your improvements and track progress over time.

The Importance of Microsoft Secure Score
Understanding why Microsoft Secure Score is crucial helps in appreciating its role in safeguarding your organisation. The Secure Score serves as a benchmark, enabling organisations to quantify and visualize their security posture in real-time. By identifying vulnerabilities and providing a clear path for remediation, the Secure Score helps prevent security breaches before they occur. It fosters a proactive approach to cybersecurity, encouraging regular assessments and continuous improvement. Moreover, the Secure Score is instrumental in aligning security practices with industry standards and regulatory requirements, ensuring compliance and promoting trust among clients and stakeholders.
By regularly reviewing and acting upon the insights provided by Microsoft Secure Score, organisations can significantly enhance their defence against identity-related cyber threats.
MicroWarehouse’s Mission 65 Program
MicroWarehouse’s Mission 65 program is designed to support businesses in achieving optimal security compliance and posture.
Objectives of Mission 65
- Achieve a Microsoft Secure Score of 65 or higher
- Implement cutting-edge Zero Trust security architectures
- Drive comprehensive security solutions
- Continuously improve your security posture
The Mission 65 program aligns with industry best practices and leverages the latest technologies to ensure businesses are well-protected against evolving cyber threats.
Take the Next Step
IT administrators and operations managers must combat threats to your business. Working with experts like Enterprise Solutions to manage your Microsoft Secure Score can improve security, protect sensitive information, and ensure operational integrity. Vigilance and proactivity are vital for safeguarding your organisation and maintaining trust.
If you’re looking to enhance your organisation’s security posture, contact us today. We can help you review your secure score and work with you to secure your environment.
Contact one of our experts today: asktheexpert@enterprise-solutions.ie

An experienced Senior Microsoft 365 engineer, specializing in cloud services such as Intune, Entra/Azure as well Microsoft’s Security products. Cormac has years of experience protecting companies against Data breach’s or dealing with the aftermath and can help your company protect its data from attacks from both outside or within.







