Alert: New Phishing Threat – Device Authentication Flow Phishing
Understanding the Emerging Threat and How to Stay Safe
It is crucial for operations managers to stay informed about the latest threats that could compromise the integrity of their organization. One such emerging threat is known as device authentication flow phishing, a new technique that is catching many off-guard in order to get access to your Microsoft 365 accounts. Here, we will shed light on this new threat and provide essential information to help non-technical operations managers guard against it.
What is Device Authentication Flow Phishing?
Device authentication flow phishing is a novel and highly deceptive phishing technique that unlike traditional phishing attacks that rely on tricking individuals into providing their credentials through fake websites or emails. In contrast, during device-code phishing attacks, the user is tricked by the threat actor to enter a device code generated by them into a legitimate sign-in portal in a similar way that you may sign into some streaming service on your television. This method can bypass traditional MFA defenses.
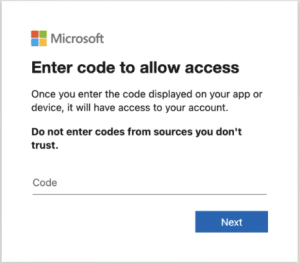
Sample dialog box showing the Device Code Authentication page.
Introducing Storm-2372
Behind many of these device authentication flow phishing attacks is a threat actor group known as Storm-2372. This group has gained notoriety for their sophisticated and persistent tactics, making them a significant concern for organizations worldwide.
Storm-2372 employs a variety of tactics to carry out their phishing campaigns. They meticulously craft emails and messages that appear to come from trusted sources within the organization, such as IT departments or executive leadership. These messages often contain urgent requests for device authentication or account verification, prompting recipients to act quickly without verifying the legitimacy of the request. Once users are redirected to a fake authentication portal, Storm-2372 captures their credentials or authentication tokens, which are then used to infiltrate the organization’s network.
Examples of Tactics Used by Storm-2372
- Email Spoofing: Storm-2372 sends emails that look like they come from internal sources, urging recipients to authenticate their devices immediately due to a supposed security issue.
- Malicious Links: The emails contain links to fraudulent authentication portals that are almost identical to the legitimate ones, making it difficult for users to distinguish between the two.
- Urgency and Fear Tactics: By creating a sense of urgency and fear, such as threats of account suspension, Storm-2372 increases the likelihood of recipients complying with the phishing attempt without proper scrutiny.
How to Protect Your Organization
Given the sophisticated nature of device authentication flow phishing, it is vital for operations managers to implement proactive measures to safeguard their organizations. Here are some steps you can take:
- Employee Education and Training
Raise awareness among employees about the threat of device authentication flow phishing. Conduct regular training sessions to educate them on how to recognize phishing attempts and the importance of verifying the legitimacy of authentication requests.
- Implement Strong Authentication Methods
Ensure that your organization uses robust multifactor authentication methods. Encourage the use of physical security keys or biometric authentication, which are less susceptible to phishing attacks.
- Block Device Flow Authentication if you don’t need it
Microsoft’s business premium and enterprise licenses give you the ability to block Device Flow Authentication if you don’t need it.
- Monitor and Respond to Suspicious Activity
Implement monitoring tools such as Microsoft Sentinel, which can can detect unusual login attempts or suspicious activities. Establish a clear response plan to address potential breaches promptly and effectively.
As cyber threats continue to evolve, staying informed and vigilant is key to protecting your organization. Device authentication flow phishing represents a significant risk, but with the right knowledge, solutions and proactive measures, you can defend against this and other emerging threats. Stay alert, stay informed, and stay secure.
The demand to protect your EUC environment and the need for strong security solutions is at an all-time high. As cyber threats become more advanced, it’s essential to stay proactive by utilizing cutting-edge technologies and best practices. Microsoft security solutions can you that peace of mind. Our team is here to guide you through the intricacies of cybersecurity, ensuring your organization remains safeguarded against potential threats.
To find out more about it how you can strengthen your organization’s security posture and avoid, contact our team of experts at asktheexpert@enterprise-solutions.ie. Our Microsoft experts are ready to assist you in implementing advanced security solutions tailored to your specific needs.

An experienced Senior Microsoft 365 engineer, specializing in cloud services such as Intune, Entra/Azure as well Microsoft’s Security products. Cormac has years of experience protecting companies against Data breach’s or dealing with the aftermath and can help your company protect its data from attacks from both outside or within.








